Encountering the fatal: detected dubious ownership in repository at '#path/to/your/repository#' error in Git can halt development workflows,
particularly after operations like cloning a repository to a new disk or when attempting to update submodules via git submodule update --init --recursive. This message indicates a security precaution implemented within Git is active.
This article delves into the reasons behind this error and outlines several effective methods to address it, ensuring you can resume your Git operations securely and efficiently.
Why This Error Occurs: Understanding Git’s Ownership Checks
The “dubious ownership” error is not arbitrary; it’s a deliberate security feature in Git. Its primary purpose is to protect users from potential vulnerabilities associated with running Git commands in repositories whose ownership is unexpected.
The Role of File Ownership
Operating systems assign an owner (a specific user ID) to every file and directory. When you execute a Git command, Git processes run under your current user account. The security check involves comparing the owner of the .git directory (and sometimes its parent directory) with the user ID of the individual running the Git command.
Git’s Security Measure (CVE-2022-24765)
Following the identification of CVE-2022-24765, Git versions (2.35.2 and later) enhanced their security by implementing this ownership check. The concern is that if a repository owned by one user (User A) is accessed by another user (User B, especially a privileged one like root), and User B runs Git commands within it, malicious code potentially embedded in User A’s repository (e.g., via Git hooks) could be executed with User B’s permissions. This error message preempts such scenarios by flagging a mismatch.
It’s important to distinguish this from file permissions (like read, write, execute, often represented by numbers like 0777). While file permissions control what actions can be performed on a file, ownership dictates who a file belongs to. The “dubious ownership” error specifically relates to this user ID ownership, not access permissions.
Read: How to Set Up Bluetooth on Ubuntu 22.04
Resolving “Dubious Ownership” Errors
Several approaches can resolve this issue, ranging from correcting file ownership to configuring Git’s trust settings. The appropriate solution depends on your specific environment and security considerations.
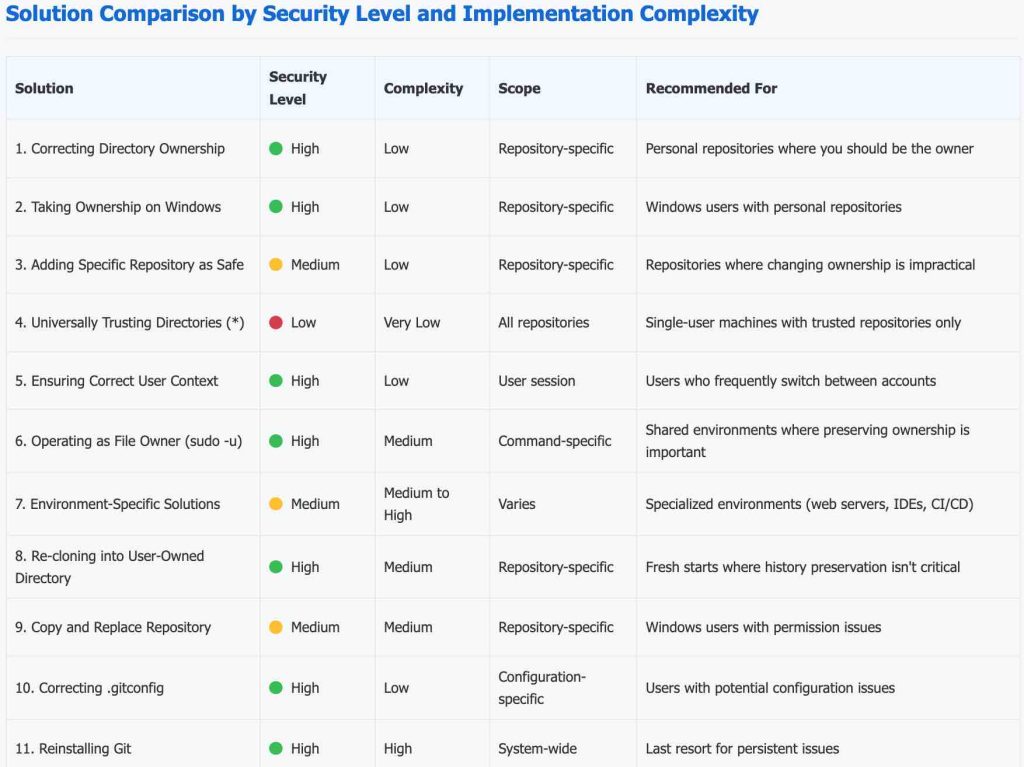
Solution 1: Correcting Directory Ownership (Linux/macOS)
If you are the intended owner of the repository files, the most straightforward solution is to update the directory ownership to match your current user.
Using chown for the entire repository
This command recursively changes the owner of the repository folder and all its contents to your current user.
sudo chown -R #your_username#:#your_group# /path/to/your/repositoryReplace #your_username# with your actual username and #your_group# with your primary group (often the same as your username). If you are already in the directory, you can use .:
sudo chown -R $(id -u):$(id -g) .It aligns the repository’s file ownership with the user executing Git commands, satisfying Git’s security check.
Targeting the .git directory and its parent
Git primarily checks the .git directory and its parent. You might need to ensure both are owned by the current user.
# For the parent directory
sudo chown #your_username#:#your_group# /path/to/your/repository
# For the .git directory and its contents
sudo chown -R #your_username#:#your_group# /path/to/your/repository/.gitSolution 2: Taking Ownership on Windows
Windows systems have their own mechanisms for managing file ownership.
Using the takeown command
The takeown command, run from an elevated (Administrator) Command Prompt or PowerShell, assigns ownership to the current user.
takeown /F "#path\to\your\repository\*" /R /AOr, if you are inside the repository directory:
takeown /F . /R /AThe /R flag makes it recursive, and /A gives ownership to the Administrators group (if run as Admin, your user is part of it). To assign to a specific user directly, you might need additional parameters or use the GUI.
If you want to take ownership for the current user specifically:
takeown /F "#path\to\your\repository" /RFollowed by granting full control if needed using icacls:
icacls "#path\to\your\repository" /grant #your_windows_username#:(F) /TIt transfers ownership of the repository files to the active Windows user, resolving the mismatch.
Using the GUI (Graphical User Interface)
- Right-click the repository folder.
- Select “Properties.”
- Navigate to the “Security” tab and click “Advanced.”
- Next to “Owner,” click “Change.”
- Enter your username, click “Check Names,” and then “OK.”
- Check “Replace owner on subcontainers and objects” and click “Apply,” then “OK.”
Read: How to Upgrade Git on Windows
Solution 3: Configuring safe.directory in Git
Git allows you to explicitly mark directories as “safe,” thereby instructing Git to trust them regardless of ownership mismatches. This configuration can be applied at different levels.
| Configuration Scope | Command Flag | File Affected (Typical) | User Impact | Privileges Needed |
|---|---|---|---|---|
| Current User | --global |
~/.gitconfig (Linux/macOS) or C:\Users\#your_username#\.gitconfig (Windows) |
Only the current user | None |
| All Users (System) | --system |
/etc/gitconfig (Linux/macOS) or Git installation’s etc/gitconfig (Windows) |
All users on the system | Administrator/root |
Adding a Specific Repository as Safe (Globally for User)
This command adds an exception for a specific repository path to your user-level Git configuration.
git config --global --add safe.directory /path/to/your/repositoryOn Windows, use the appropriate path format, for example:
git config --global --add safe.directory C:/Users/#your_username#/path/to/repoIt tells Git that you vouch for the safety of this particular directory, bypassing the ownership check for it.
Adding a Specific Repository as Safe (System-Wide)
To apply this setting for all users on the machine (e.g., for service accounts or shared environments), use the --system flag. This usually requires administrative privileges.
sudo git config --system --add safe.directory /path/to/your/repositorySolution 4: Universally Trusting Directories (Use with Caution)
Git allows a wildcard (*) to mark all directories as safe. This effectively disables the ownership check system-wide or for the current user.
* reduces Git’s security protections. This approach should only be considered if you fully understand the implications, typically on a single-user machine where you control all repositories. It is generally not recommended for shared systems or drives containing repositories from multiple sources.Globally for the Current User
git config --global --add safe.directory '*'Note: Some terminals, especially on Windows, might require double quotes: git config --global --add safe.directory "*".
System-Wide for All Users
This requires administrative privileges.
sudo git config --system --add safe.directory '*'Directly Editing .gitconfig
You can also manually add this to your Git configuration file (~/.gitconfig for global, or /etc/gitconfig for system):
[safe]
directory = *Or, for a specific directory:
[safe]
directory = /path/to/your/repositoryIt broadly instructs Git to bypass ownership checks, treating all (or specified) directories as safe.
Read: How To Fix ‘Filename too long’; Errors in Git on Windows
Solution 5: Ensuring Correct User Execution Context
Sometimes, the error arises because Git commands are unintentionally run as a different user.
Switching Users (Linux)
If you were temporarily using root (e.g., via sudo su) or another user account, switch back to your standard user account that owns or should own the repository.
su #your_standard_username#It ensures Git commands are executed by the user who is expected to own the repository files.
Consistent User Execution (Windows)
If you cloned a repository using an Administrator Command Prompt but are now trying to use Git via a GUI tool running as your standard user (or vice-versa), ownership conflicts can occur. Ensure you operate on the repository consistently with the same user context or adjust ownership accordingly.
Solution 6: Operating as the File Owner with sudo -u (Linux)
If you must run Git commands as your current user, but the files are owned by another (e.g., a service account like jenkins), you can execute the Git command as the owner user without changing your current shell user.
sudo -u #owner_username# git #your_git_command_here#Example:
sudo -u jenkins git pullThe Git command is executed under the identity of the file owner, satisfying the ownership check for that specific command execution.
Solution 7: Addressing Specific Environments and Tools
Different tools and environments might require specific handling:
- Web Servers (e.g.,
www-datawith PHP): If PHP scripts execute Git commands, thewww-datauser (or equivalent) must either own the.gitdirectory or the repository path must be added to the system-widesafe.directorylist.sudo chown -R www-data:www-data /path/to/your/repository/.git # Or, for system-wide trust: sudo git config --system --add safe.directory /path/to/your/repository - IDE and GUI Client Considerations:
- IntelliJ, VS Code, etc.: These tools often use their own bundled Git or the system’s Git. Ensure the
safe.directorysettings are applied to the correct Git configuration (user global, system, or sometimes an IDE-specific one). If CLI commands to setsafe.directorydon’t resolve IDE issues, manually editing the relevant.gitconfig(e.g.,C:\Users\#Your_Username#\.gitconfig) might be necessary. - Sublime Merge (Windows): May require editing its own
gitconfigfile, often located in its installation directory (e.g.,C:\Program Files\Sublime Merge\Git\etc\gitconfig), to add the[safe]section. - Fork Client (Windows with WSL): If accessing a WSL repository from the Fork Windows client, you might need to add the WSL path to the Windows Git configuration used by Fork. This is done from a Git console within Fork:
git config --global --add safe.directory '%(prefix)///wsl$/#Your_WSL_Distro_Name#/#path/to/repo/in/wsl#' - JetBrains Rider (and similar IDEs): If an IDE was previously run as Administrator and then switched to a standard user (or vice-versa), this can trigger the error. Running the IDE consistently as the intended user for the project, or fixing ownership, is key.
- IntelliJ, VS Code, etc.: These tools often use their own bundled Git or the system’s Git. Ensure the
- CI/CD Pipelines (e.g., GitHub Actions): In automated environments, using
git config --system --add safe.directory '#repository_path#'is often more appropriate than--globalas the execution user might vary or lack a persistent home directory.
Solution 8: Re-cloning into a User-Owned Directory
If the repository is located in a problematic directory (e.g., a mounted drive with restrictive default ownership), consider cloning it into a directory you own directly, such as within your home directory.
mkdir ~/new-repo-location
cd ~/new-repo-location
git clone #your_repository_url#Ensures the repository is created with the correct ownership from the outset.
Solution 9: Windows Workaround: Copy and Replace Repository
On Windows, sometimes copying the repository to a temporary location and then moving it back can reset ownership to the current user.
# In Git Bash or a similar shell on Windows
cp -r /path/to/problematic/repo /path/to/temporary/location
rm -rf /path/to/problematic/repo
mv /path/to/temporary/location /path/to/problematic/repoThe copy operation often creates new files owned by the user performing the copy.
Solution 10: Verifying and Correcting .gitconfig Integrity
Incorrect entries or syntax errors in your .gitconfig file can prevent safe.directory settings from working.
- Inspect your global (
~/.gitconfigorC:\Users\#your_username#\.gitconfig) and system (/etc/gitconfig) files. - Look for duplicate
[safe]sections or malformeddirectory = ...lines (e.g., missing slashes, incorrect path quoting). - Use
git config --global --editorsudo git config --system --editto open the configuration file in an editor for review and correction.
Example of a correctly formatted section (multiple directories):
[safe]
directory = /path/to/repo1
directory = C:/path/to/repo2
directory = *Ensures Git can correctly parse and apply your intended safety exceptions.
Solution 11: Reinstalling Git (Last Resort)
In rare cases, if configurations are deeply tangled or if there’s a suspicion of a corrupted Git installation, reinstalling Git and re-applying necessary configurations (like email, name, and minimal safe directory settings if still needed) can be a final troubleshooting step.
It provides a clean slate for Git’s configuration and binaries, potentially resolving obscure issues.
Verifying the Solution
After applying a solution, the simplest way to verify its effectiveness is to re-run the Git command that initially triggered the “dubious ownership” error. For instance:
git submodule update --init --recursiveIf the command executes without the error, the issue is resolved.
Important Considerations
While resolving the “dubious ownership” error is crucial for productivity, it’s equally important to understand the security implications of certain solutions. Disabling the check globally (safe.directory = '*') should be a carefully considered decision, reserved for environments where the risk is understood and accepted (typically single-user, locally managed machines).
Prioritizing solutions that correct ownership (chown, takeown) or grant specific exceptions (safe.directory /path/to/repo) is generally safer than globally disabling the check.
Conclusion
The “fatal: detected dubious ownership in repository” error in Git is a safeguard against potential security vulnerabilities related to file ownership. By understanding that this check compares the repository owner’s user ID with that of the Git command executor, you can choose the most appropriate solution.
Whether it’s adjusting file ownership, configuring Git’s safe.directory settings, or ensuring commands run under the correct user context, the above methods provide comprehensive ways to resolve this issue and maintain a secure and functional Git workflow.




